Imagine for a moment that you are a hacker, an ethical one. You are called upon by law enforcement to hack into a business network known to be engaged in criminal activity for financial gain as its primary activity. Assume you are not to be concerned with any politics of the job and that your actions are legal and ethically justified. This nefarious business takes its own security seriously and therefore has implemented several forms of network security. These include firewalls, Web proxies for its Web gateways, and VPNs for remote users. You also know that this business exists much like any normal corporation, renting several floors of office space to accommodate between 100-200 employees. Also imagine that the business’s entire network topology is located in that same location. Your goal is to infiltrate the security sufficiently to find evidence included in the local MSQL database. You need to remain anonymous and operate within the reasonable parameters of the law.
Essay Writing Service Features
Our Experience
No matter how complex your assignment is, we can find the right professional for your specific task. Writing Errands is an essay writing company that hires only the smartest minds to help you with your projects. Our expertise allows us to provide students with high-quality academic writing, editing & proofreading services.
Free Features
Free revision policy
$10Free bibliography & reference
$8Free title page
$8Free formatting
$8How Our Essay Writing Service Works
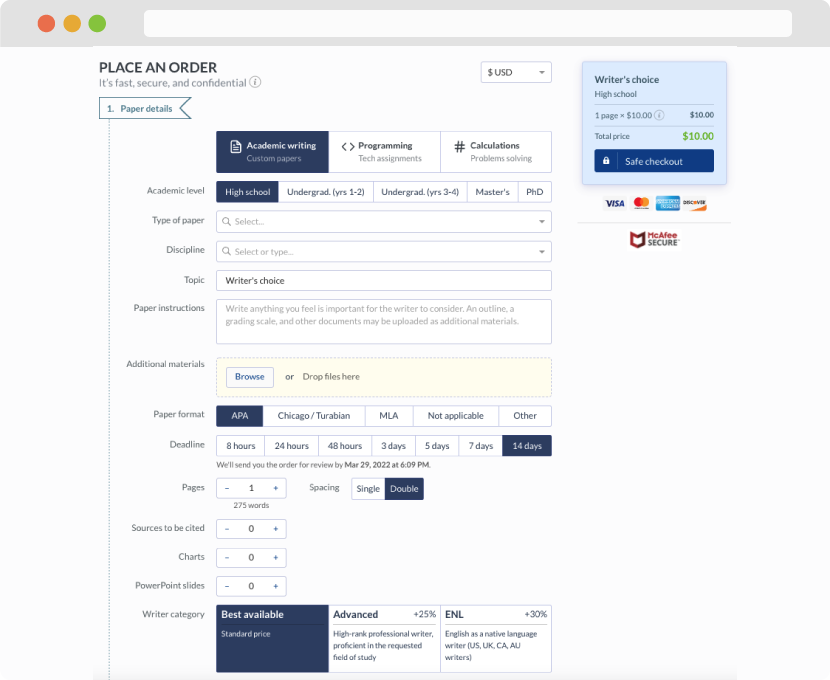
First, you will need to complete an order form. It's not difficult but, in case there is anything you find not to be clear, you may always call us so that we can guide you through it. On the order form, you will need to include some basic information concerning your order: subject, topic, number of pages, etc. We also encourage our clients to upload any relevant information or sources that will help.
Complete the order form
Once we have all the information and instructions that we need, we select the most suitable writer for your assignment. While everything seems to be clear, the writer, who has complete knowledge of the subject, may need clarification from you. It is at that point that you would receive a call or email from us.
Writer’s assignment
As soon as the writer has finished, it will be delivered both to the website and to your email address so that you will not miss it. If your deadline is close at hand, we will place a call to you to make sure that you receive the paper on time.
Completing the order and download